Modern business can hardly be imagined without computers, tablets, smartphones, storage devices and other gadgets that provide access to the Internet.
However, the rapid growth of digitalization of the global and Ukrainian economy has another side. It increases cyber threats, cyber attacks, and other violations of cybersecurity, namely the secure handling of data in cyberspace. These negative consequences affect all: citizens, businesses, and the state as a whole. In 2023, 19% of all global cyberattacks were aimed at Ukraine, making us the second most affected country after the United States.
Government agencies, banks and financial organizations, online retailers, IT companies, businesses that deal with personal data of customers, manufacturing companies, and startups are the most affected by cyberattacks.
Large-scale cyberattacks against Ukrainian government agencies and businesses have intensified since the beginning of russian aggression. Cybercriminals plan these attacks to paralyze the work of strategic facilities and business companies. According to the State Service for Special Communications, the number of cyber incidents registered in Ukraine in 2023 increased by 62.5% compared to 2022 (1105 cyber incidents in total). For comparison: the number of cyber incidents in 2022 was 2.8 times more than in 2021.
These statistics indicate that every Ukrainian company should be aware of its vulnerabilities and assess them in advance to protect its systems from cyber incidents and technological failures. A vivid example of how a cyberattack can lead to devastating consequences is the destruction of the IT infrastructure of Kyivstar mobile operator due to a cyberattack on December 12, 2023.
The following are the most used attack vectors:
- Malware (or malicious software) is unauthorized software installed into a system without anyone's knowledge. It can be hidden in legal sources or attached to the files. There are many types of malware to fulfill different cybercrime goals, such as replicating or encrypting files, blocking legitimate user access, or stealing sensitive data.
- Ransomware is a form of malware designed to encrypt files on a computer. As a result of this cyberattack, the perpetrators demand a ransom to gain access to them.
- Viruses — these malicious programs replicate themselves and infect files and systems, often making a computer impossible to operate.
- Denial of Service (DoS) attacks are malicious cyberattacks that spam a network with false requests to disrupt business operations.
- Phishing — this cyberattack is based on imitating legal sources to access sensitive data, such as passwords and credit card information, via phone, email, SMS, and social media.
- Internal threats. Although many cyberattacks come from external sources, intentional and unintentional threats exist inside the organization. Employees may have access to the network and sensitive data and sell it for financial gain. Unintentional insider threats are often associated with negligence.
The experience of BDO in Ukraine confirms that to withstand cyber attacks, businesses need not only the advanced hardware and software, but also comprehensive protection of the main areas where cyber threats are implemented.
What does the BDO Digital team recommend?
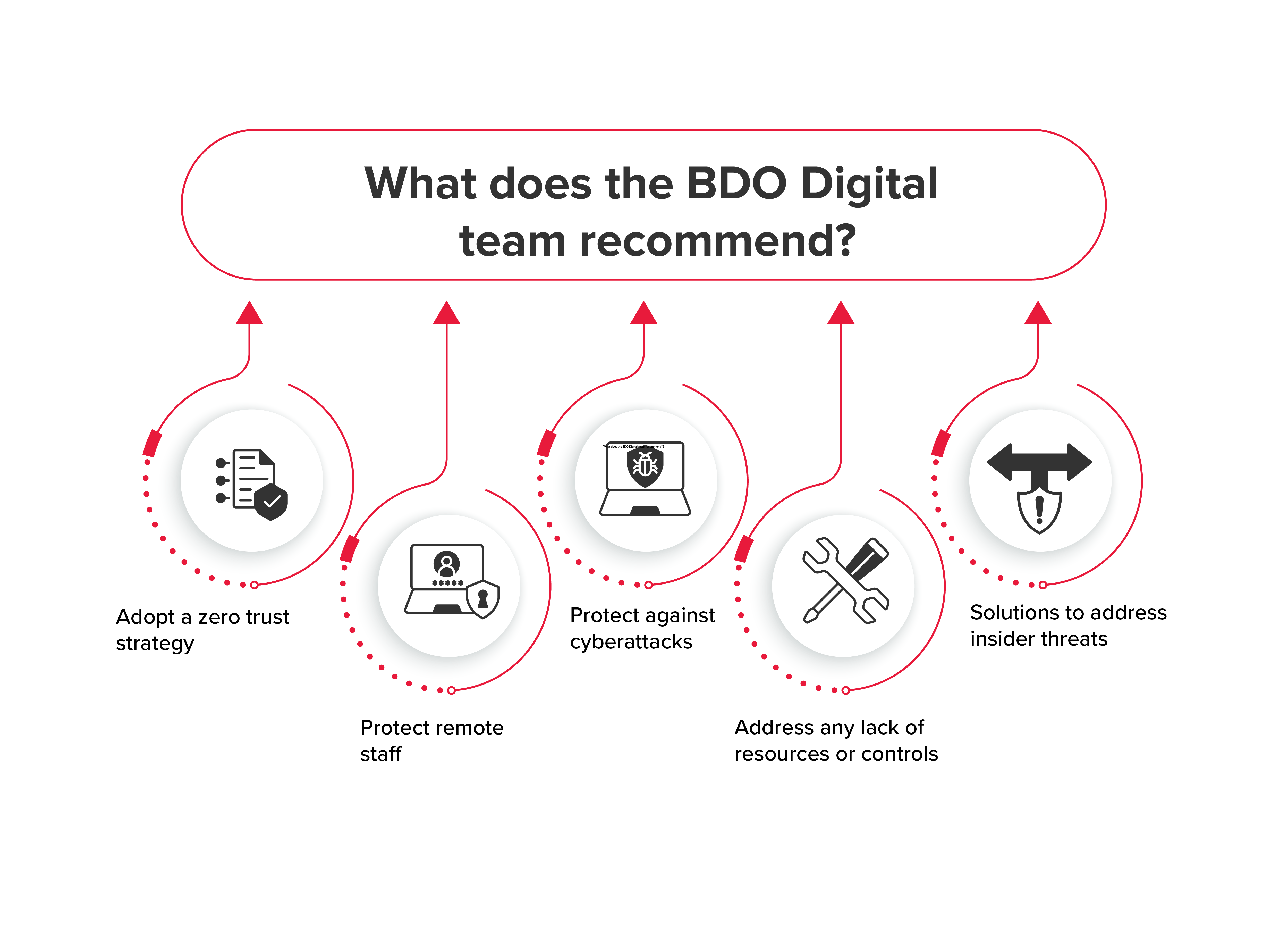
1. Adopt a zero trust strategy
Implementing a zero-trust strategy means shifting to a broad security model that will allow enterprises to limit access to valuable applications, data, and company environments. This will be done in a way that does not jeopardize employee productivity or user experience.
2. Protect remote staff
Implement software to prevent data loss to monitor, detect, and respond to potential data breaches, and endpoint security should be implemented to protect the company's network from threats coming from employee or customer devices.
3. Protect against cyberattacks
Multi-factor authentication (MFA) is a must for cybersecurity. MFA allows an organization to grant electronic access to websites or applications only after providing two or more forms of proof of identity. Security training for employees is also essential as it will ensure that employees are always aware of any relevant or important cybersecurity steps, for example, making sure that all employees are using email security best practices.
4. Address any lack of resources or controls
If an organization is struggling to find the controls or resources to develop or manage a security strategy, consider developing an ongoing managed security strategy and operating it. However, avoid the usual “set it and forget it” approach. A security strategy should be updated and adjusted over time. To ensure this, consider partnering with a security specialist. BDO Digital offers the services of cyber specialists who can provide ongoing security analysis, leading to better decision-making around business objectives.
5. Solutions to address insider threats
Insider threats are complex, they are based on human nature and do not follow a pattern that can be identified. Most insider threats are motivated by financial gain, although there are other reasons behind such behavior.
Some possible prevention methods are as follows:
- Culture changes: a robust security culture within a company is essential to mitigate the potential damage caused by insider threats. Employees will be less prone to random threats and will be more aware of suspicious behavior by other colleagues.
- Protecting critical assets: in many cases, data must be accessible to several employees. Take digital security measures to protect your own assets and customer data. Whenever an employee resigns from the company, take appropriate steps to terminate his/her access to sensitive data as soon as possible.
- Behavioral tracking: increase transparency across the organization to understand what employees are doing. Behavioral analytics and machine learning provide insight into the aggregate of common data activities across an organization, making it easier to track down unusual activity.
If you're concerned about any of these insider threats, you can contact BDO Digital experts to create an action plan for your organization based on your individual security needs.