The global BDO network hosted a webinar entitled “Secure by design Closing the gaps in digital transformation webinar”, focusing on integrating cybersecurity into digital transformation initiatives and managing generative AI risks.
In partnership with BDO and the international market analytics provider IDC (International Data Corporation), practical insights into the current state of security and digital transformation were gathered.
Among the speakers, representatives from the BDO network: Wayne Anderson (Managing Director, Cybersecurity, BDO USA), Brad Storan (Head of Offensive Security & DFIR, BDO UK) і Jason Gottschalk (Partner, Cybersecurity, BDO UK) shared their conclusions on business readiness for cyber threats, discussed current challenges in implementing artificial intelligence (AI), and presented practical strategies for improving cyber resilience.
IDC Survey coverage and methodology
The IDC survey covered seven countries — Canada, the United States, the United Kingdom, Australia, Germany, the Netherlands and Belgium — and included representatives from 15 industries, with organisations ranging in size from 100 to more than 5,000 employees. The study surveyed 411 respondents, all having responsibility for or influence over cybersecurity within their organisations, ensuring a high level of representativeness and strong practical value of the results.
What IDC’s cyber readiness study revealed
The focus is on IDC’s white paper Cybersecurity Readiness and the Age of Digital Transformation (July 2025), based on a survey of 411 respondents across seven countries and multiple industries. Among the most notable findings are:
- Only 40% of organisations integrate cybersecurity at the digital transformation planning stage, which often leads to delays and disruptions during implementation.
- In doing so, 31% of companies have already implemented GenAI usage policies, indicating that the pace of innovation is outpacing effective risk management.
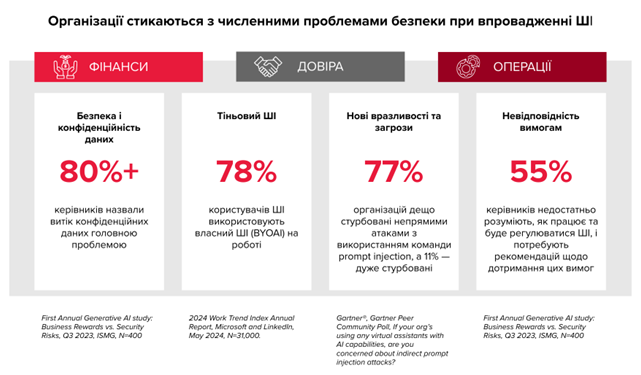
- Of the 81% of organisations that rate their cybersecurity budgets as adequate or better, only 26% feel very confident in their readiness for cyber threats.
- These organisations report more than five incidents per year, emphasising that the decisive factor is not the level of spending, but the degree of operational readiness.
Generative AI: shadow use and attack modelling
The speakers highlighted the key risks of GenAI and introduced two important concepts — Shadow AI and AI Red Teaming — which are especially relevant for organisations today. Shadow AI refers to the use of AI tools and models without formal approval, proper management, or adequate controls. While it may boost productivity, it also creates significant security and compliance risks.
At the same time, AI Red Teaming is viewed as an effective way to address these challenges. By testing and modelling malicious scenarios, organisations can identify vulnerabilities in AI systems and enhance the security of their implementation.
As an example of this trend, research from early 2024 shows that 78% of users bring their own AI tools into their work processes.
- 31% of organisations have already implemented policies governing employee use of GenAI.
- According to the survey, 77% of organisations are concerned about the risk of prompt injection, with an additional 11% being very concerned.
- For GenAI solutions, it is crucial to implement AI Red Teaming and testing practices, such as the OWASP Top 10 for LLMs.
Practical steps to turn spending into real readiness
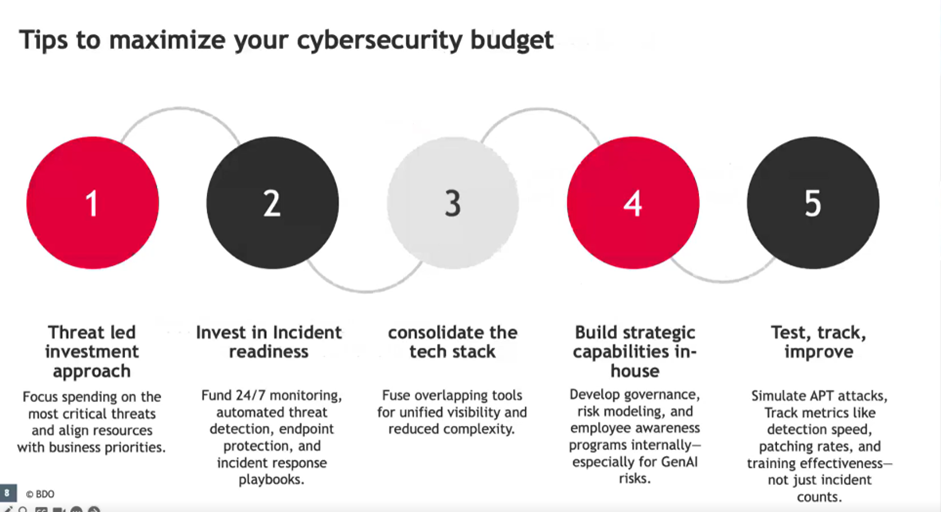
- Threat-led investment approach: Focus your budget on the most critical threats and align spending with your organisation’s business priorities.
- Invest in incident readiness: Invest in 24/7 monitoring, automated threat detection, endpoint protection, and response playbooks.
- Consolidate the tech stack: Integrate tools with overlapping functions to achieve unified visibility and reduce complexity.
- Build strategic capabilities in-house: Strengthen governance, risk modelling, and staff awareness programmes, with a particular focus on GenAI risks.
- Test, track, improve: Model APT attacks, track metrics (detection rate, patching rate, training effectiveness) — not just the number of incidents.
The most popular risk minimisation strategies
The most common practices organisations use to mitigate risks associated with artificial intelligence include employee training (49%), the implementation of specialised AI-specific security solutions (46%) and strengthening data access controls (41%). At the same time, only 31% of organisations have formalised usage policies, highlighting the urgent need to close gaps in AI governance and usage policies.

Challenges on the path to sustainability
Organisations — particularly medium-sized and large enterprises — continue to face fundamental security challenges. These gaps persist despite adequate budgets and board-level oversight, highlighting a disconnect between strategy and implementation.
- Third-party risk management
- Vulnerability remediation
- Secure by design

Fundamentals of modern sustainability
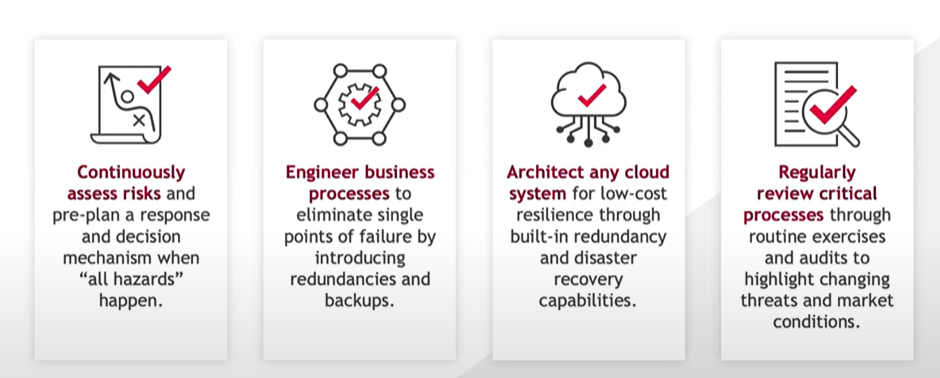
- Constantly assess risks and pre-plan a response and decision mechanism when “all hazards” happen.
- Engineer business processes to eliminate single points of failure by introducing redundancies and backups.
- Architect any cloud system for low-cost built-in redundancy and disaster recovery capabilities.
- Regularly review critical processes through routine exercises and audits to highlight changing threats and market conditions.
Experts of BDO in Ukraine emphasise that the effective and secure implementation of artificial intelligence requires a systematic approach combining risk management, mature corporate governance, continuous monitoring, and the development of cyber resilience. AI presents significant business opportunities only when security is integrated into strategy, processes, and corporate culture. This approach transforms cybersecurity from a reactive function into a strategic tool that supports long-term growth and builds trust.
BDO in Ukraine recommends:
- Implement a comprehensive approach to cybersecurity that focuses on the most critical business threats.
- Ensure transparency across supply chains and properly assess third-party risks.
- Invest in employee training and modern security tools, including AI solutions.
- Regularly update security policies and test their effectiveness.
For more information on cybersecurity measures and recommendations, contact the team of BDO in Ukraine for a consultation.



























